In the first blog post of this series I have given you an overview of the InMage Scout architecture. In this blog post I will show you how to set up the protection for a Linux VM.
After you have successfully installed your Linux Master Target start the vContinuum console.
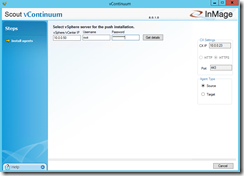
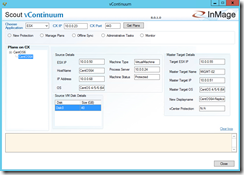
Navigate to Administrative Tasks and click on Push Agent. A new window will come up where you have to enter the IP address of your ESXi host or of your vCenter server and the credentials. Select Source as Agent Type and click on Get Details
Afterwards you expect to see the VMs on the ESXi host, but vContinuum currently does not support the push agent installation onto Linux.
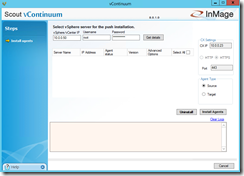
If you want to do the push agent installation then you have to use the management website. Navigate to SETTINGS –> Push Install or Upgrade Agents. Click on Install Agent and choose the appropriate Push Server for the push agent installation.
Choose the operating system and type in the IP address of the Linux VM. Click on submit. Now you have to enter the root credentials which will be used for the agent installation.
In the next step you choose Unified Agent as Agent Type, Scout Agent as Agent Features and check if the Configuration Server IP address, the Communication Mode and the Port Number are set correctly. Click on Next and on the next page on Run.
The installation will not succeed because of the forgotten entry in the /etc/hosts file. You will see the following error message in the logs.
Could not Open build file at
(INFO) Successfully Sent HostName to CX.
(INFO) successfully recieved Install Details from CX
Initializing…
(INFO) Downloading of Build from CX..(INFO) Install Type: FreshInstall
-i 10.0.0.23 -p 443 -a host -t both -s Y -d “/usr/local/InMage/” -c https
The Downloaded build extracted successfullyThe installation of /tmp/remoteinstall/InMage_UA_8.0.1.0_RHEL6-64_GA_26Feb2015_Release.tar.gz is about to start..
********************
UA INSTALLATION
********************
——————————————————————-
Fri Apr 17 19:49:50 CEST 2015
——————————————————————-
Host name ( CentOS64 ) does not match with IP address 10.0.0.68 in /etc/hosts
installer /tmp/remoteinstall/InMage_UA_8.0.1.0_RHEL6-64_GA_26Feb2015_Release.tar.gz exited with exit code 256
It is the same case as it was during the configuration of the Linux Master Target.
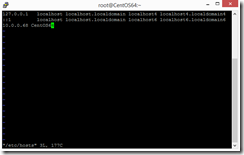
Before you install the Unified Agent on the Linux VM you have to edit the file /etc/hosts and add the following entry.
“IP address Master Target” “Hostname Master Target”
10.0.0.68 CentOS
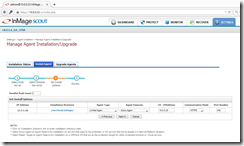
Mark the Linux VM and click on retry. The installation of the Unified Agent succeeds now.
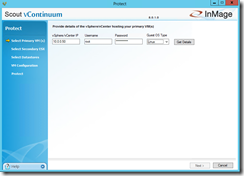
After the successful agent installation on your Linux VM click on New Protection in the vContinuum console. A new window will come up where you have to enter the IP address of your ESXi host or of your vCenter server and the credentials. Select Linux as Guest OS Type and click on Get Details.
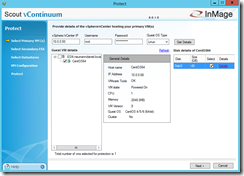
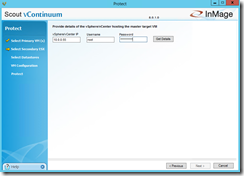
Afterwards you should see the Linux VM on the ESXi host and you can select the disks of the VM you want to protect. It is possible to select several VMs at this step. On the next page enter the IP address of your ESXi host at the DR Site or of your vCenter server and the credentials. Click on Get Details.
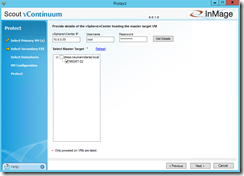
Afterwards you should see the Linux Master Target on the ESXi host and you can select your Linux Master Target that you want to use for the protection of the Linux VM.
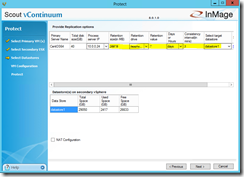
Under Select Datastores you define all the settings that are required for the protection. First of all select the correct retention drive. Then you can define the retention value in days or hours. I would recommend to use days. Before you calculate the retention size and enter it you should choose the consistency value. Depending on the workload requirements you can enter different values for different VMs. My recommendation would be 5 minutes. The lowest value you can enter is 2 minutes.
The retention size can be calculated in two ways. It is the same procedure as for the size of the retention volume on your Master Target. First one is change rate in GB * retention range in days. Second one is source disk sizes * change rate in percentage * retention range in days.
- 2,8 GB * 7 days = 19,6 GB
- 60 GB * 0,07 * 7 days = 19,6 GB (0,07 = 7%)
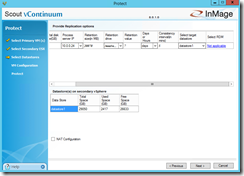
Before you proceed select the right datastore that provides enough free space for the Linux VM. If you have more than one Process Server you can select one of them in the column Process server IP.
As you can see the VM does not have any Raw Device Mapping disks. But you can protect VMs with VMDKs and / or RDMs.
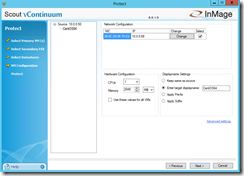
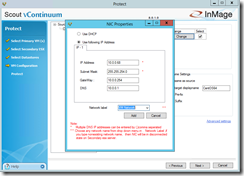
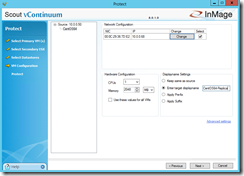
In the VM Configuration section you can set the hardware and network configuration settings for the Linux VM at the DR site.
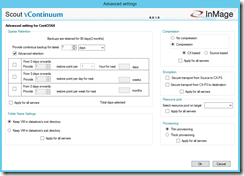
You can also define the display name and set additional advanced settings for the protection. Per default all data will be compressed but not encrypted and the Linux VM disks will be thin provisioned on the DR site.
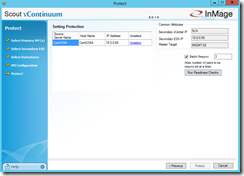
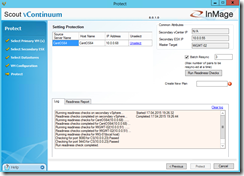
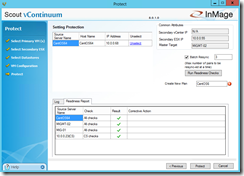
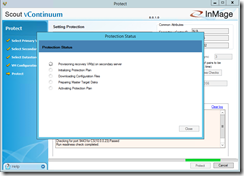
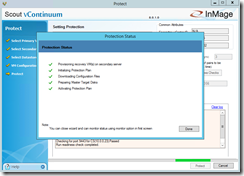
Before you can start the protection you have to run some readiness checks under the the section Protect. If the checks complete successfully define a name for the protection plan. For more details about the readiness checks click on Readiness Report. Now you can click on Protect to start the final configuration processing.
When one of the steps during the final configuration processing fails you can directly jump into the log via a link to get more details about the failure.
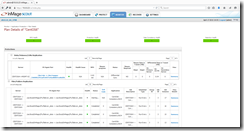
You need more information about the protection plan? Click on the VM under the protection plan in the vContinuum console.
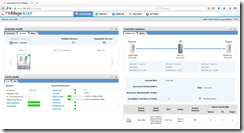
After the successful protection activation go back and log in into the management portal. In the management portal click on Servers under Protection Health and select the Linux VM. On the right site under Protection Summary click on Protection Details.
You can see the actual protection status for each replication pair. The initial replication consists of two steps Resyncing (Step I) and Resyncing (Step II). You can see this in the column Status under Disks/Volumes/LUNs Replication. The initial replication is completed after the status changed to Differential Sync and Data Consistency Health and Retention Health at the top of the page changed from grey to green.
The next and last blog post in this series will be about the different DR options Recover, Failback Protection and DR-Drill.